The rise in the value of cryptocurrencies has consequently pursued large groups of cybercriminals to hack crypto coins like Bitcoin and Monero. More and more investors all over the world are swarming to buy crypto tokens but the lack of proper knowledge puts them at a massive risk. In the era of digital currency, it is very important to know how anyone with just some technical knowledge about browser mining scripts can easily hack crypto within minutes.
Cryptojacking is in fact one of the most unnoticed crimes going around. It is essentially an online threat that hides on a computer or mobile device utilizing the resources of that device to “mine” and hacks crypto tokens. Criminal crypto miners often use web browser downloads or rogue mobile applications to come through. This means they can access and hack crypto assets that you own on any of your devices, including desktops, laptops, smartphones, and even network servers.
Profit is the obvious motive behind this incredible rise in criminals who want to hack cryptocurrencies. There are investors in the crypto game who have invested hefty amounts without being aware of the risks. The main skill of crypto hacks lies in staying completely incognito from the owner of the crypto coins.
This has resulted in huge numbers of searches across all engines about how to hack crypto coins. In order to protect your own crypto coins, you should have a detailed concept of the various ways by which hackers can hack crypto coins, and, even potentially steal them.
How to Hack CryptoTab?
CryptoTab is an amazing and unique browser with many similarities to the Google Chrome browser. The CryptoTab browser lets its users access their favorite sites online and also equally pays them for doing that using Bitcoin.
Earning through CryptoTab isn’t much complicated at all and is quite legit. All you need to do is open the app and start the mining engine. But in order to earn sufficient cryptocurrency, it might take some time initially since the mining speed is especially low.
You can hack the CryptoTab browser easily using scripts. There exists a vulnerability in it where it can record your keystrokes and transfer your crypto tokens to a different account. These scripts are available online in many places. Thus, the loose security system puts the cryptocurrency you own at massive risk.
This leads hackers to hack crypto assets through CryptoTab using techniques to boost and hack Crypto Tab mining speed.
In order to hack the Cryptotab, see the following steps:
- First, you’ll need to download the Official paid version of the CryptoTab Pro browser. Then go to your CryptoTab Dashboard and click on the Start Mining button.
- Make sure to have a VPN from beforehand as it will make your process of setting up HTTPCanary a lot easier in the next steps.
- After installing HTTPCanary, accept their License Agreement and proceed to configure the MITM or Man in the Middle, also known as a VPN.
- Install the HTTPCanary root certificate and enter your phone lock PIN/Pattern/Fingerprint.
- Once you are in the main UI of the app, click on the hamburger icon at the top left side and click on Target Apps.
- Locate and add CryptoTab browser to the list of targeted apps. Now your next job is to set up the mining scripts.
- The mining scripts are dependent on the packages captured by the HTTPCanary app. You can capture these packages by clicking on the Tweet button at the right bottom screen in the main UI of the HTTPCanary app.
- After filtering out the unnecessary data, select Server Host.
- Now, all you need to do is select any POST connection weighing less and enter the coding of the scripts available online.
- Once you’ve entered all the necessary values, Save the modifications, and your work is done.
Although the process might look hectic, even novice hackers can hack crypto assets in your CryptoTab browser using this technique.
How to Hack Crypto Coins?
Cryptocurrency tokens rely on blockchain technology primarily that uses a peer-to-peer system for verifying transactions instead of the traditional way of using banks. Blockchain transactions are usually regarded as extremely secure, unalterable, and even, unhackable.
Sadly, your crypto tokens are definitely not completely hack-proof. In fact, your money is stored in digital wallets makes it a much easier target than hacking the entire blockchain technology.
So, how can you hack crypto? Let’s take a look at the different ways hackers employ to hack crypto tokens and get access to your money.
1. Using Phishing to Hack Crypto
The most effective way by which hackers try to hack crypto assets focuses on making people give out access themselves. This is possible through the forgery of legitimate-looking websites that look authentic but are a trap for you to enter your credentials.
These emails containing links to a fake website to hack your crypto coins are delivered to potential targets where they often end up entering sensitive information. We recommend you avoid this by being attentive always and carefully checking the domain spelling (like http://binnance.net instead of https://binance.com ) and SSL certificate.
2. Using Mobile Applications to Hack Crypto
Not all the crypto trading mobile applications that you find are secure. This is largely due to the poor architecture and security backdoor which makes it very vulnerable to crypto hacks. Hackers often use a number of ways from brute-force attacks to guessing the PINs or performing unauthorized actions to break past the security layers.
You can easily hack crypto coins belonging to anyone within an application with unencrypted databases and get a hold of their API keys and other sensitive information.
3. Using Malware and Viruses to Hack Crypto
Old but gold, malware infections still rank among one the most widespread methods hackers use to hack crypto tokens you own. They can infect your device using keyloggers and steal personal information like passwords and PINs.
4. Stealing Secret Keys to Hack Crypto
Performing any financial operations with cryptocurrency requires you a pair of keys- public and private. The private key is available only to the holder and is used as a digital signature to authorize all transactions. The public key, on the other hand, is used to confirm the private one.
This private key is usually stored in crypto wallets. Losing this key means instantly losing all your crypto assets.
Hackers use various ways starting from browser extensions, applications with spell checkers and common system vulnerabilities to hack crypto and get access to your Private key. Hot crypto wallets that are connected to the Internet and running on a centralized system are the easiest targets for such types of hackers.
Can Blockchain be Hacked?
Yes. In fact, blockchain hacks recently have drastically increased owing to the vulnerabilities existing within the system. In January 2022, the massive international cryptocurrency exchange Crypto ended up losing $ 30 million worth of cryptocurrency from the digital wallet of 483 users. Major US Twitter accounts were also once hacked during a Bitcoin scam.
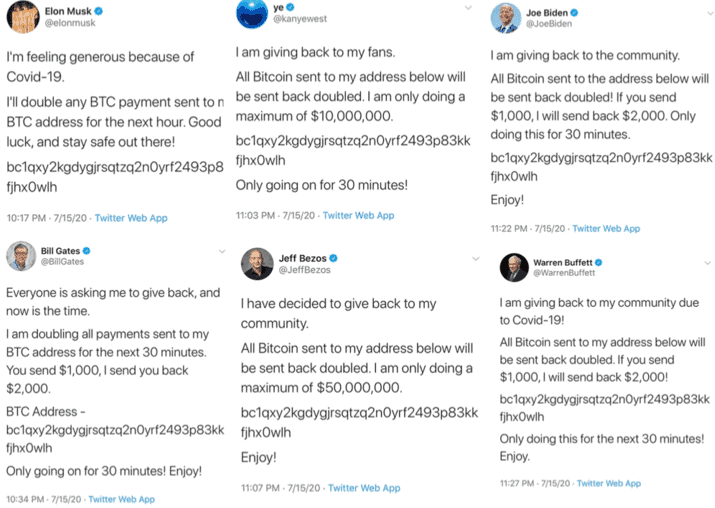
This recent activity illustrates that blockchain technology is definitely not unhackable. If you are a crypto investor, you should always be cautious, especially while trading on exchanges. You should check out more ways of generating income through GMT Investments here.
Different Scenarios of Blockchain Hack:
- 51% attacks: These types of attacks are common on smaller-scale blockchains because it is much harder for miners to gain control over complex and large blockchains. If one or more hackers manage to get access to over half of the mining process, there can be gravely negative consequences. Hackers can even double-spend cryptocurrency as they can create an entirely different set of transactions by designating it as the true version of the blockchain.
- Lack of Security: Many blockchain exchanges are endowed with insufficient security to the unawareness of the investors. This makes such platforms an easy target for hackers to hack crypto assets and have access to your data.
- Creation Errors: Larger and more intricate blockchains usually face a lot of security glitches or errors during their creation. When this occurs, hackers try to identify the vulnerability and perform their attack. Smart Contracts are particularly easy targets since hackers can easily hack crypto without being detected through security flaws and steal your assets during their operations.
Final Thoughts
Hackers being able to hack crypto assets might seem like a relatively harmless crime. But in the digital era, where more and more of your assets are becoming digitalized, we recommend you follow good cybersecurity practices to minimize the risk of crypto jacking.
By protecting yourself against both browser mining and standalone crypto-mining malware, you can definitely stop cybercriminals from accessing your system. There have been widely publicized frauds, scams and hacks that have affected major individual investors and cryptocurrency exchanges in a short span of time. With new technologies always emerging on the Internet, you have to be extremely cautious to stop hackers from being able to hack crypto assets you own.
FAQs
1. Can you hack Bitcoin?
Although hacking Bitcoin is hard, if hackers can determine some of your non-crypto currency-related personal information, they can easily hack crypto tokens of Bitcoin kept in your digital wallets.
2. How to protect myself against crypto hacks?
You can protect your crypto assets from getting hacked by blocking JavaScript in your browser. Popular programs like “No Coin” and “MinerBlock” also help to block mining activities in popular browsers. The latest version of Opera browsers has NoCoin built-in.
3. How to detect if someone has hacked my crypto?
You can easily detect if your crypto assets are getting hacked. Simply lookout for symptoms like decreased performance, overheating, increased CPU usage and more.
Share with us if you have encountered any incident of crypto hacks in your lifetime.


Cryptocurrency tokens depend on blockchain technology basically that utilizes a shared system for confirming transactions rather than the conventional approach to utilizing banks. Blockchain transactions are typically viewed as very secure, unalterable, and even, unhackable.